
A Beginner’s Guide to Safely Accessing the Darknet
Welcome to this guide on how to safely access the part of the internet known as the darknet. The darknet is a hidden network of websites that requires special software to visit. While it has a reputation for illicit activities, it is also used by journalists, activists, and privacy-conscious individuals to communicate securely and bypass censorship.
The key to accessing the darknet is a tool called Tor, which stands for "The Onion Router."
What is Tor and How Does it Work?
Think of the internet like a postal service. When you visit a normal website, it's like sending a postcard. Anyone who handles it—your internet service provider (ISP), the government, or network administrators—can read the message and see who sent it and where it's going.
Tor, on the other hand, is like sending your message in a sealed envelope, inside another sealed envelope, inside yet another. Your connection is bounced through several volunteer-operated servers around the world, with a layer of encryption added at each step. This makes it nearly impossible for anyone to trace your activity back to you or see what you are doing online.
Websites on this network use the special .onion domain instead of .com or .org.
Step-by-Step Guide to Accessing the Darknet
Step 1: Download and Install the Tor Browser
This is the most important step. You must get the browser from the official source to avoid malicious versions.
Go to the Official Website: Open your regular web browser (like Chrome, Firefox, or Safari) and go to
https://www.torproject.org.Download the Browser: Find the download link for your operating system (Windows, macOS, or Linux) and save the file to your computer.
Install the Software: Once the download is complete, open the file and follow the installation instructions. It installs just like any other program.
Important: Never download the Tor Browser from any source other than the official Tor Project website.
Step 2: Connect to the Tor Network
When you launch the Tor Browser for the first time, you won't be online immediately.
Launch Tor Browser: Open the application you just installed.
Connect: A window will pop up. Simply click the "Connect" button.
Be Patient: It may take a minute or two to connect as the browser establishes a secure, anonymous path through the network. Once connected, the browser window will open, and it will look and feel very similar to Firefox.
You are now connected to the Tor network!
Step 3: Browse the Darknet
You cannot find .onion websites using Google. These sites are unlisted, and their addresses are often long, complicated strings of letters and numbers (e.g., u2uaeeuh2hnvdo24jaojizy3x6j6r52v7w3er5meegjlgkk3lmhrilid.onion).
Use a Darknet Search Engine: Start with a trusted search engine that specializes in indexing
.onionsites. A popular and reputable one is Ahmia. You can also use DuckDuckGo's onion version for added privacy.Find Directories: Look for "link lists" or directories that curate and categorize
.onionsites. However, be aware that many links may be broken or lead to unsafe places.
Crucial Safety Rules for Every User
Your anonymity depends on your actions. Follow these rules strictly.
Rule #1: NEVER Share Personal Information. Do not use your real name, email address, password, or any identifying details on any
.onionsite. Assume everything you type can be seen by the site's owners.Rule #2: Consider Using a VPN (Virtual Private Network). A VPN encrypts your connection and hides your online activity from your Internet Service Provider (ISP). While Tor hides what you are doing, a VPN can hide the fact that you are using Tor in the first place, adding an extra layer of privacy. Connect to your VPN first, then open the Tor Browser.
Rule #3: Do NOT Download Anything. Files downloaded from the darknet have a very high risk of containing viruses, spyware, or other malware designed to compromise your security and deanonymize you.
Rule #4: Do NOT Change Browser Settings. Do not install browser extensions or plugins. Do not resize the Tor Browser window from its default dimensions. These actions can be used to "fingerprint" your browser and identify you among other Tor users.
Rule #5: Be Skeptical of Everything. Scams are extremely common on the darknet. If a service or product seems too good to be true, it is a trap. Do not trust anyone.
Rule #6: Stick to Legal Activities. The darknet contains a vast amount of illegal and disturbing content. Accessing or engaging with such material can have severe real-world consequences. This guide is for educational and privacy purposes only.
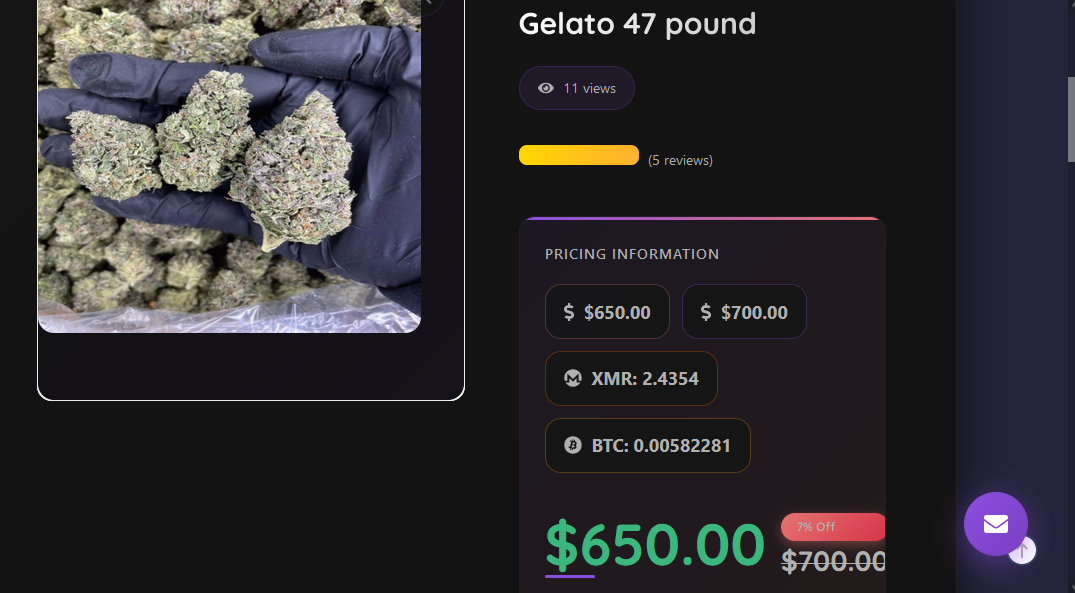
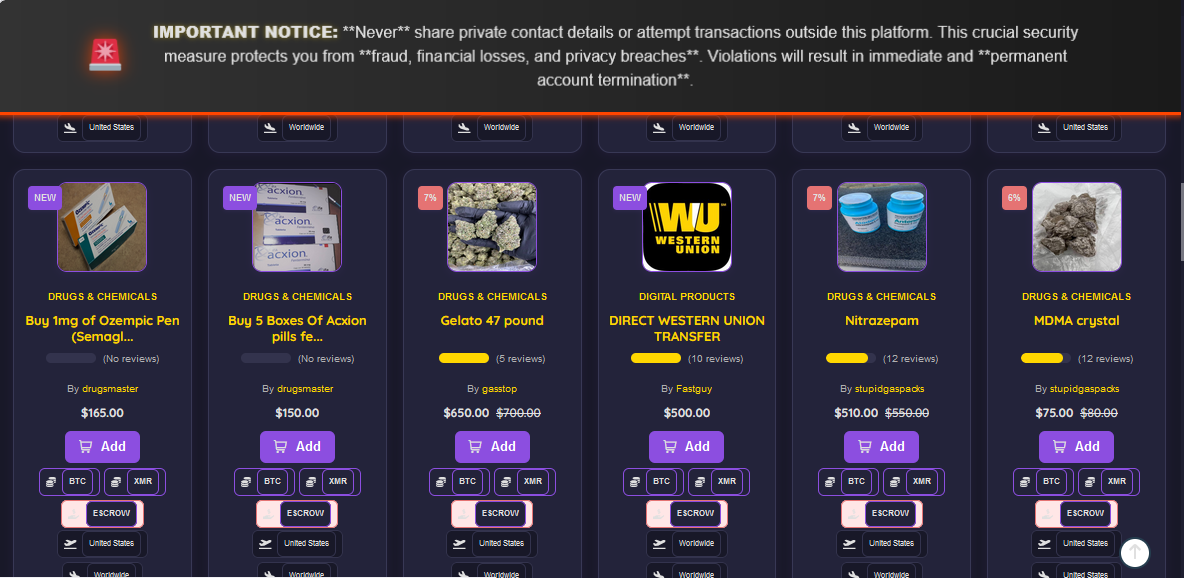
Top Dark web markets links
Velox Market is the darknet’s most trusted destination for fast, secure, and anonymous shopping. From exclusive digital goods to rare products you won’t find anywhere else, every order is protected by our unbreakable escrow system, ensuring you never get scammed. With BTC and Monero support, verified vendors, and 24/7 live support, you get peace of mind with every purchase. Pages load instantly. Orders move fast. Messages stay encrypted. No risk — just results.
Official URL: http://u2uaeeuh2hnvdo24jaojizy3x6j6r52v7w3er5meegjlgkk3lmhrilid.onion/
Piranha Market is the darknet’s rising predator — built for those who demand anonymity, reliability, and power. We combine cutting-edge technology with uncompromising security to bring you a 100% escrow-protected multivendor marketplace where trust isn't optional — it's enforced.
Official URL: http://m2idoel3w63jjwzq2h7vbtf3vcfw2bylya4fvrxy4aqvjh5vdbwpqnad.onion/
By following these steps and rules, you can explore the privacy-enhancing side of the internet while minimizing the significant risks involved. Stay safe and browse smart.






Write a comment ...